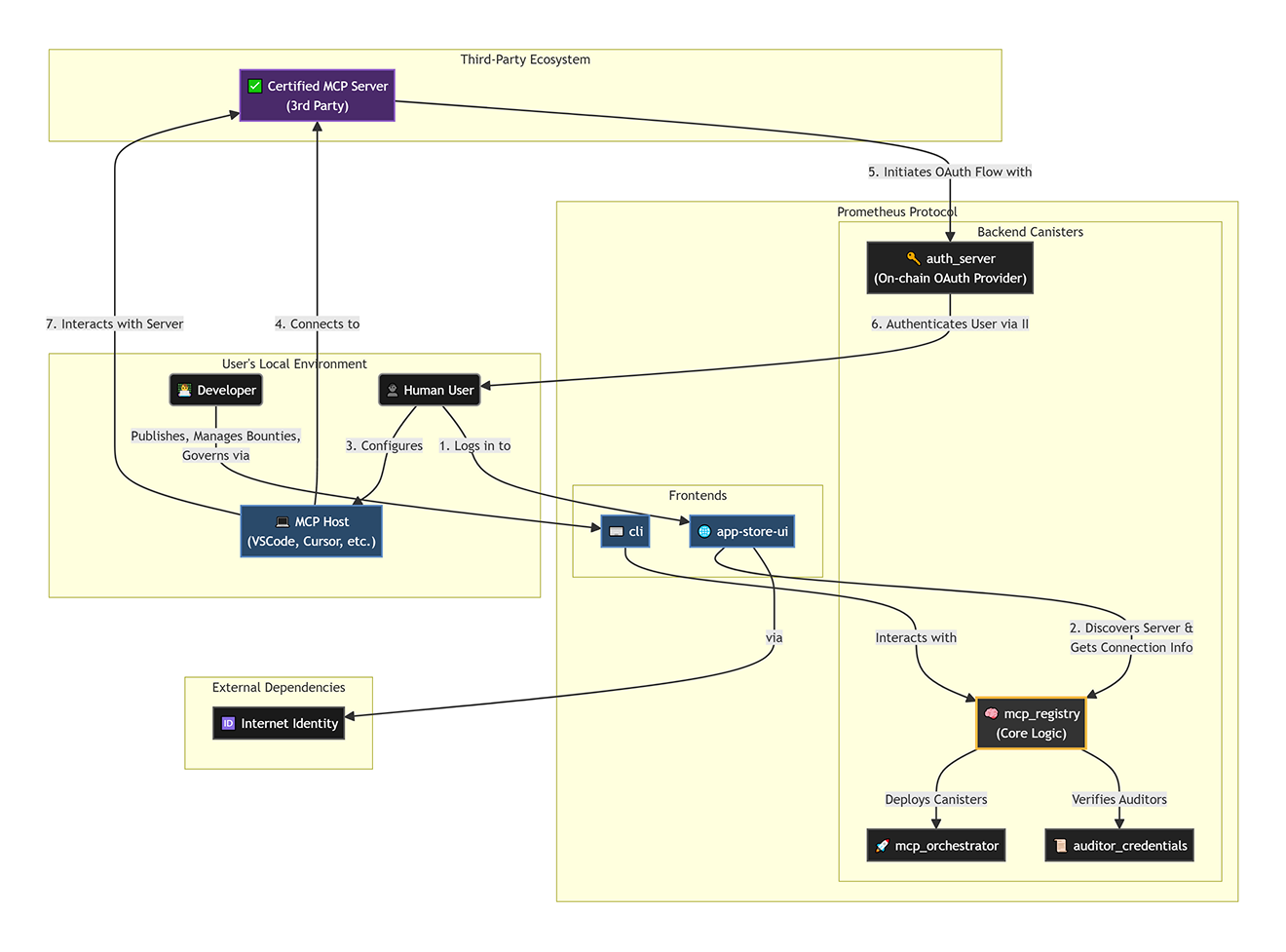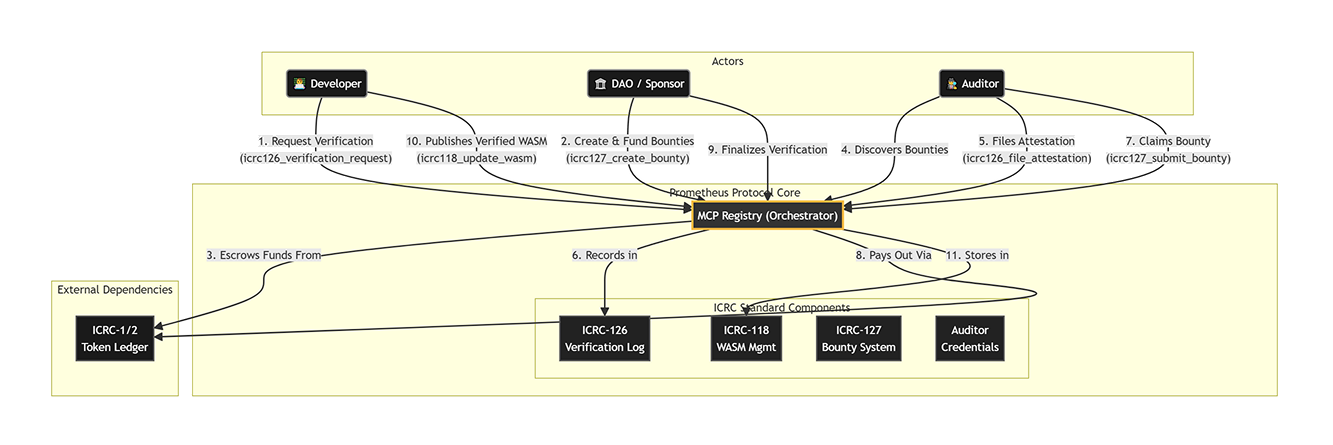
Core Components
The protocol is composed of several key on-chain services working in concert to provide the pillars of identity, trust, and payments.The Identity Provider
An on-chain service that issues and validates credentials. It provides both
API Keys for programmatic clients and OAuth 2.1 tokens for interactive user
sessions.
The Trust & Deployment Hub
The core of the trust layer. It manages the service registry, the audit and
bounty lifecycle, and the secure deployment pipeline that takes verified
code and deploys it to the mainnet.
The Verification Network
A decentralized network of automated verifier bots that perform reproducible
builds using Docker. These bots monitor the registry for pending
verifications, rebuild WASMs from source, and file cryptographic
attestations on-chain—earning token rewards for their work.
The Audit Hub
An economic incentive layer built on ICRC-126 (attestations) and ICRC-127
(bounties). It manages bounty creation, verifier staking, consensus
tracking, and automated reward distribution for both build verification and
security audits.
Identity & Interaction Model
A critical concept in the Prometheus architecture is the distinction between two types of identity:- Protocol Participant Identity: The identities of developers and auditors who build and secure the ecosystem.
- End-User & Agent Identity: The identities of the final consumers who interact with the services listed in the App Store.
1. Protocol Participants (The “Supply Side”)
Developers, verifiers, and auditors interact directly with the protocol’s core services to perform supply-chain functions. This on-chain, verifiable process is our answer to the need for an “intentional design” for the agent economy. It builds the foundation of trust necessary for an open ecosystem to thrive.- Actions: Publishing code, performing automated builds, claiming bounties, submitting audit results.
- Identity & Tools: These actions are authorized using the blockchain’s native identity system (principals). However, the tools used differ by role:
- Developers use the Prometheus CLI to perform command-line operations like publishing new service versions with
app-store-cli release. - Verifiers run automated bots that continuously monitor for pending verifications, perform Docker-based reproducible builds, and file attestations—earning token rewards.
- Auditors use the Prometheus web UI (the Audit Hub) to find and claim bounties, review code, and submit their security audit results.
- Developers use the Prometheus CLI to perform command-line operations like publishing new service versions with
2. End-Users & Agents (The “Demand Side”)
When an end-user or an AI agent wants to use a service from the App Store, they need a more user-friendly and standards-based way to authenticate. This flexible, standards-based identity is the key to unlocking an open “Web of Agents.” Unlike the locked-in identities of “walled gardens,” our Identity Provider acts as a universal passport, allowing any user or agent to securely interact with any service on the network.- Actions: Calling a paid tool, granting payment allowances.
- Identity: The protocol’s on-chain Identity Provider facilitates this. Service developers integrate with it to support two flows:
- API Keys: For programmatic agents to make authenticated requests.
- OAuth 2.1: For human users to have a familiar, secure login experience.